What is a NIS 2 Directive
In today’s interconnected world, the digital realm has become an indispensable part of our daily lives, powering everything from critical infrastructure to personal communications. With this reliance on digital systems comes an inherent vulnerability to cyberattacks, a threat that looms large over businesses and public entities alike. To fortify Europe’s cyber defenses and enhance resilience against these ever-evolving threats, the European Union has introduced the Network and Information Security 2 (NIS 2) Directive.
Understanding the NIS 2 Directive
The NIS 2 Directive serves as a cornerstone of the EU’s cybersecurity strategy, aiming to establish a harmonized framework for cybersecurity risk management across member states. Building upon its predecessor, the original NIS Directive, NIS 2 expands its scope and introduces stricter requirements to address the growing complexity and sophistication of cyber threats.
Purpose and Objectives
At its core, the NIS 2 Directive is driven by the overarching goal of enhancing the overall cybersecurity posture of the European Union. It seeks to achieve this through a multi-faceted approach that encompasses:
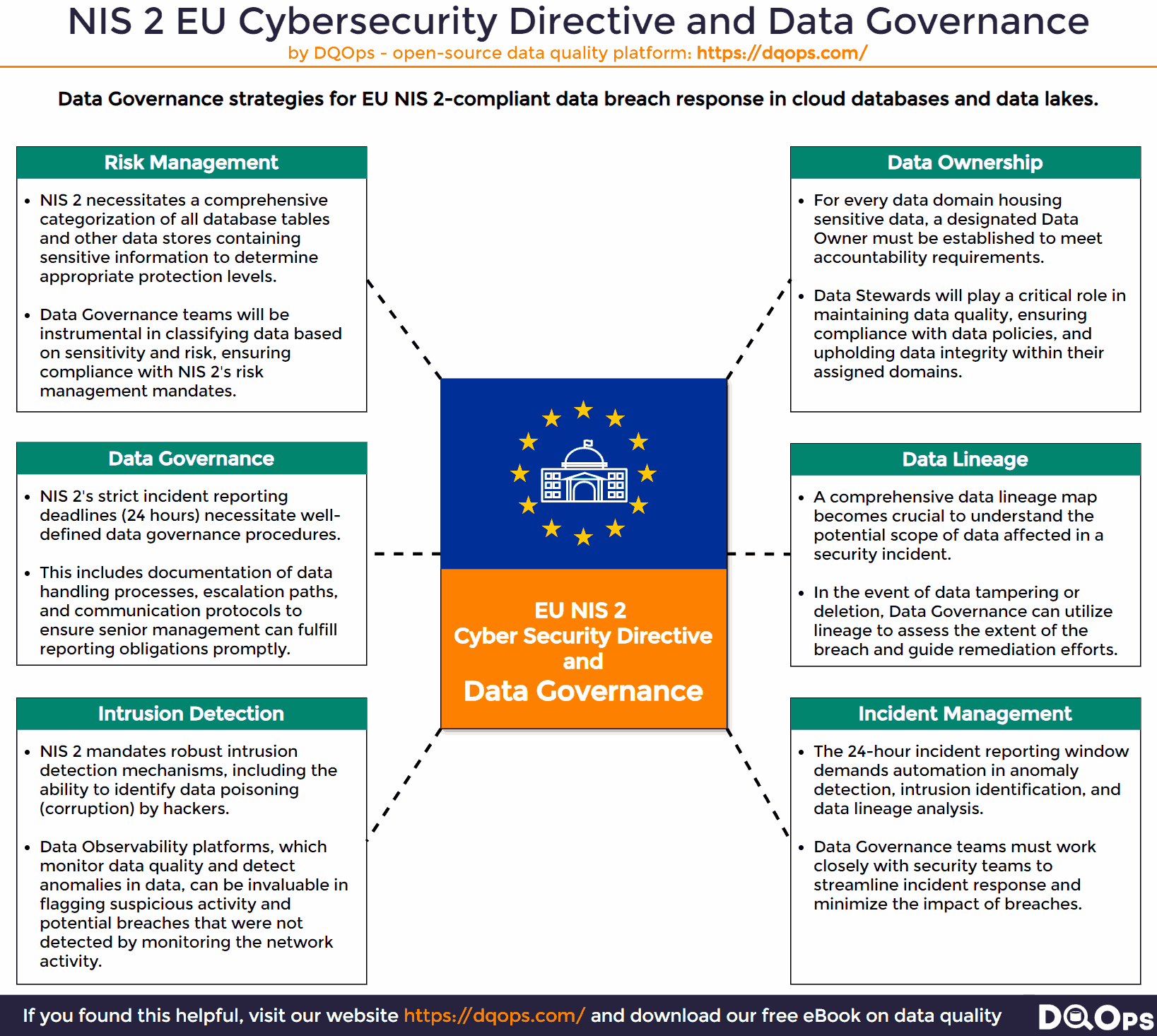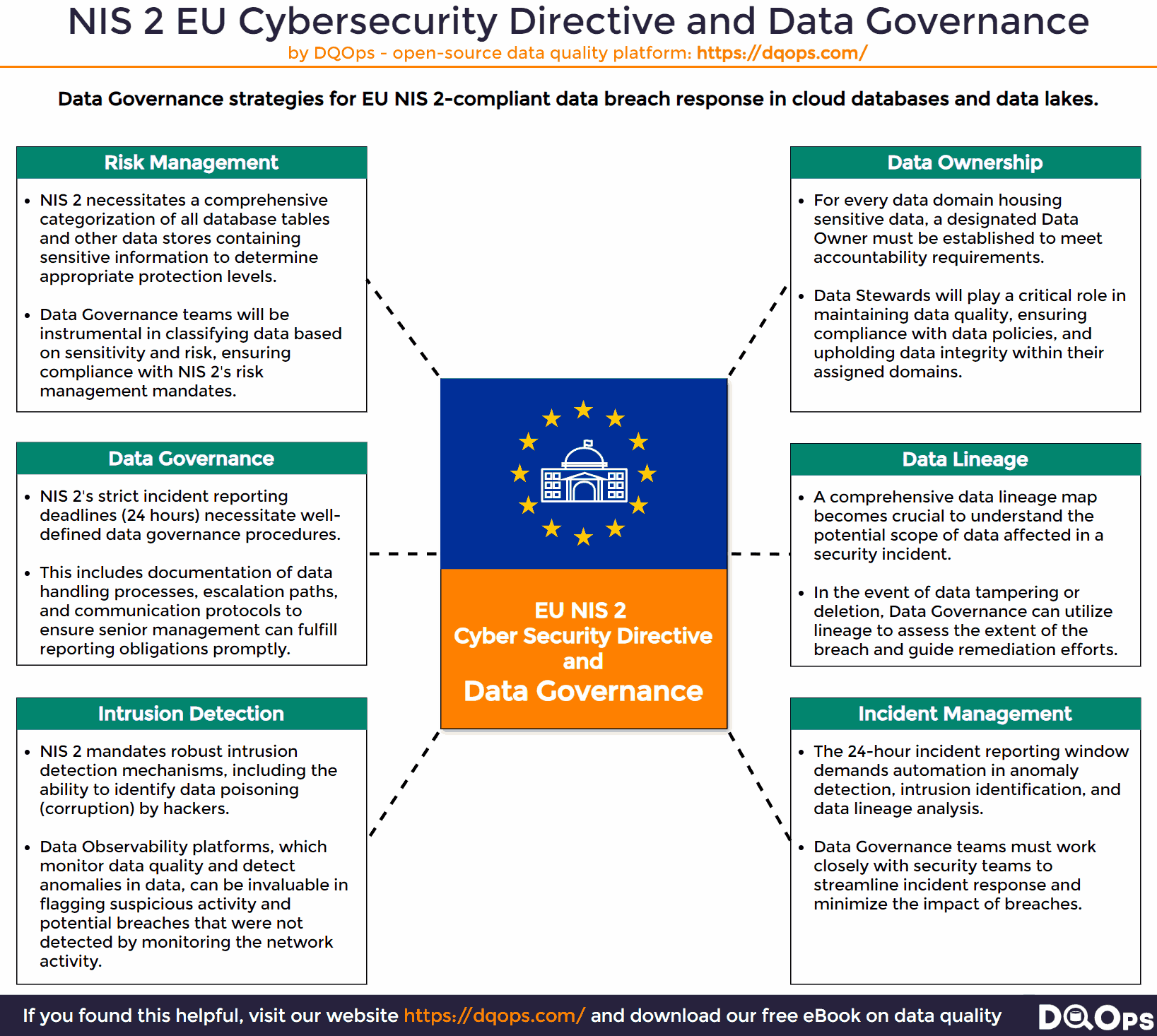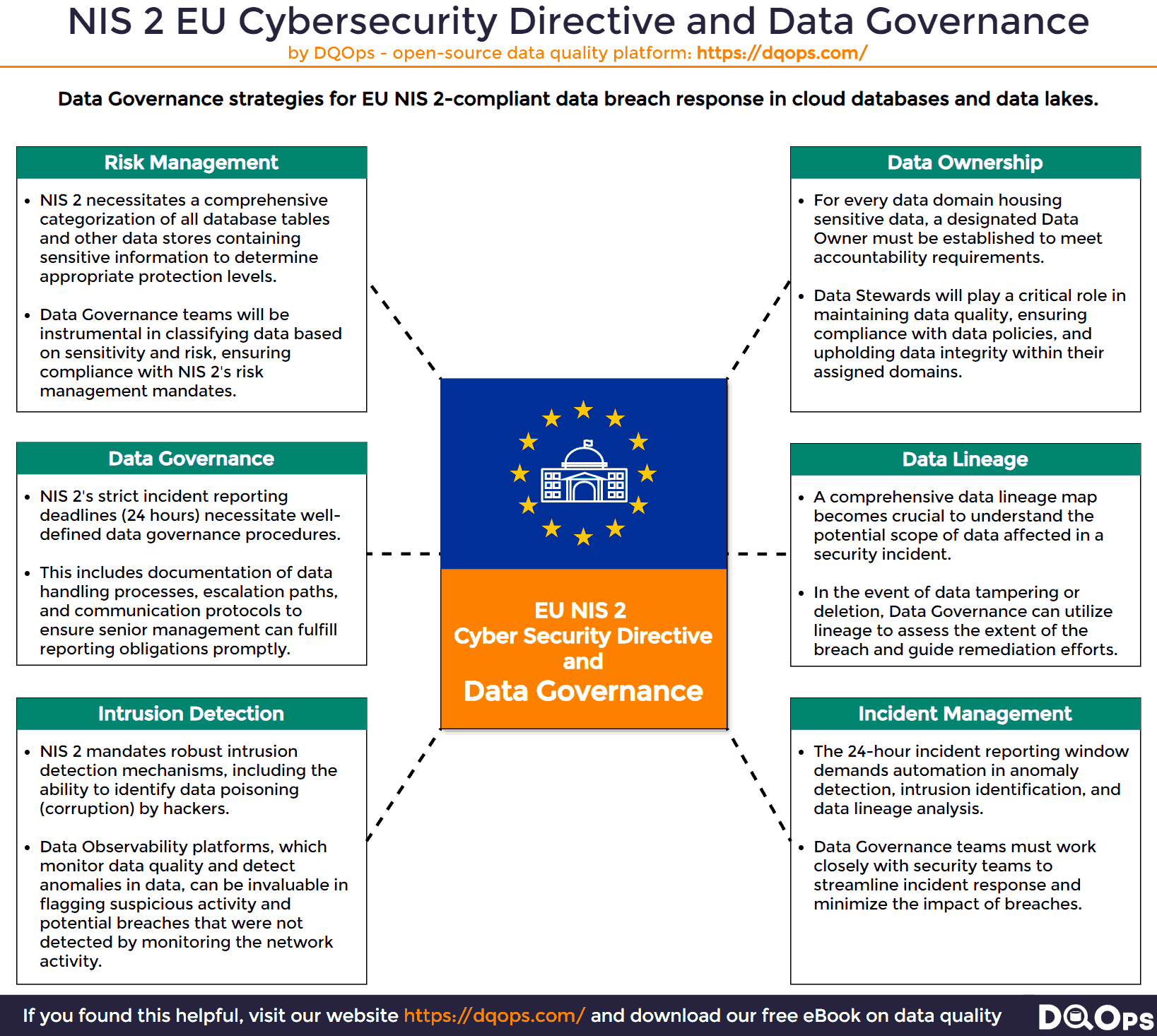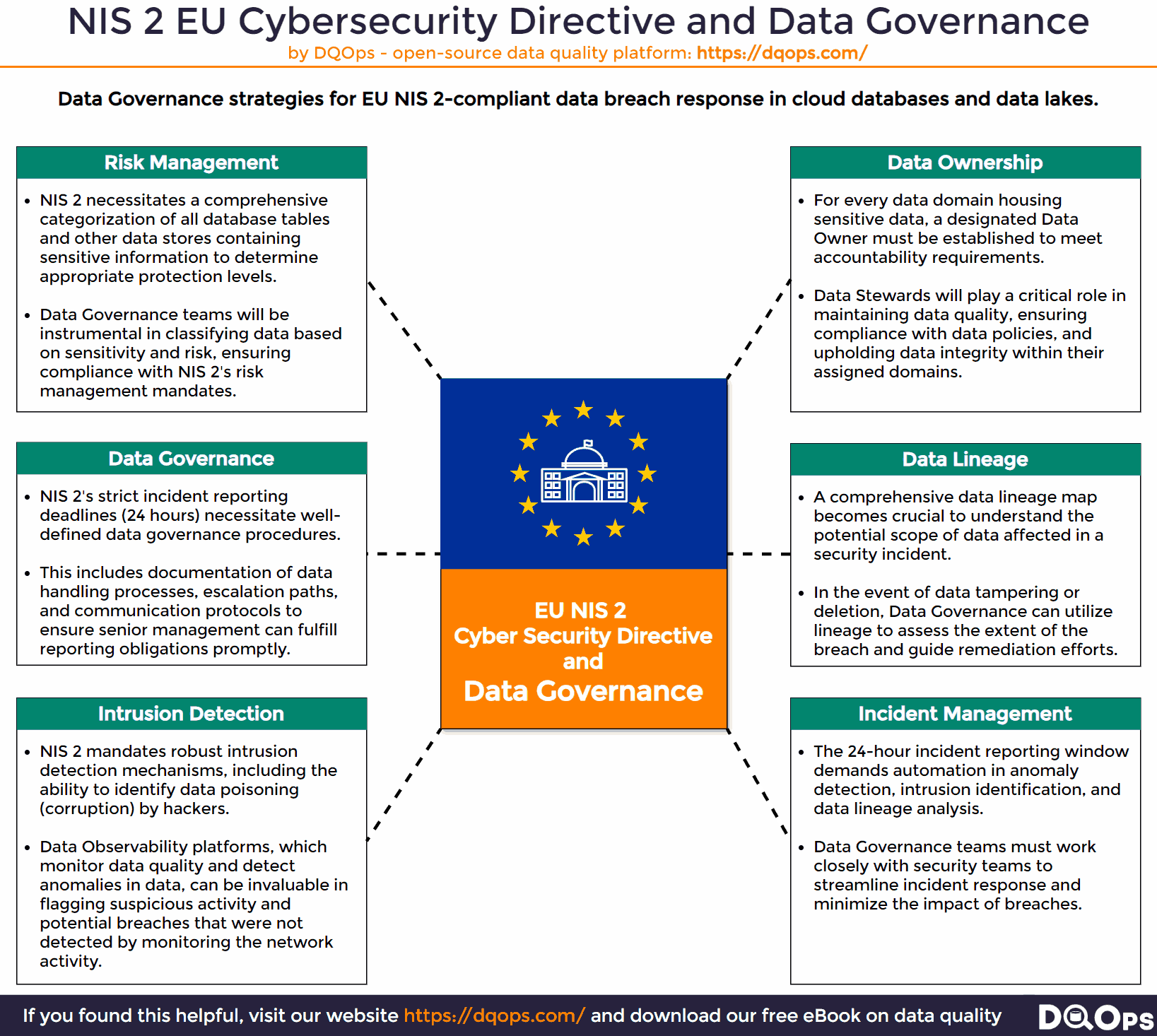
- Risk Management: NIS 2 mandates organizations to adopt a risk-based approach to cybersecurity, requiring them to identify, assess, and manage risks proactively.
- Security Measures: The directive outlines a set of baseline security measures that organizations must implement to mitigate risks and protect their networks and information systems.
- Incident Reporting: NIS 2 introduces mandatory incident reporting obligations, ensuring that significant cybersecurity incidents are promptly reported to relevant authorities.
- Cooperation and Information Sharing: The directive emphasizes the importance of cooperation and information sharing between member states and relevant stakeholders to foster a collective defense against cyber threats.
By establishing a robust and unified cybersecurity framework, the NIS 2 Directive strives to create a more secure and resilient digital landscape for Europe, safeguarding critical services and protecting individuals and businesses from the potentially devastating consequences of cyberattacks.
NIS 2 Directive: Key Deadlines for Implementation
While the NIS 2 Directive’s purpose is clear, its implementation timeline is crucial for organizations to understand. The directive sets forth specific deadlines that member states and affected organizations must adhere to:
- Member States: The deadline for Member States to transpose the NIS 2 Directive into their national laws is October 17, 2024. This means that each EU country must have its own legal framework in place to enforce the requirements of the directive by this date.
- Organizations: Following the transposition into national laws, organizations will then need to comply with the specific requirements outlined in their respective member state’s implementation. While the exact timeline may vary slightly across member states, organizations should expect to be fully compliant by late 2024 or early 2025.
It’s critical to note that these deadlines are rapidly approaching. Organizations that fall within the scope of NIS 2 should be actively preparing for compliance to avoid potential penalties and disruptions to their operations.
NIS 2 Directive: Who Must Comply?
The NIS 2 Directive casts a wide net, encompassing a broad range of industries and organizations considered essential for the functioning of society and the economy. These entities are classified into two main categories:
Essential Entities
- Energy: This sector includes electricity, district heating, oil, gas, and renewable energy generation, transmission, and distribution operators.
- Transport: Companies providing essential transport services such as air, rail, water, and road transport.
- Banking: Credit institutions and investment firms.
- Financial Market Infrastructures: Central securities depositories, central counterparties, and trading venues.
- Health: Healthcare providers, including hospitals, medical service providers, and laboratories, as well as manufacturers of medical devices, pharmaceuticals, and in-vitro diagnostic medical devices.
- Drinking water: Water supply and distribution operators.
- Wastewater: Wastewater treatment and management entities.
- Digital infrastructure: Providers of domain name system (DNS) services, cloud computing services, content delivery networks (CDNs), and data centers.
- Public administration: Central and regional public administration bodies, including digital public services.
- Space: Space-based services such as satellite communications, earth observation, and navigation services.
- Postal and courier services: Providers of postal and courier services.
Important Entities
In addition to Essential Entities, NIS 2 also identifies a second category known as “Important Entities”. These entities are also considered critical, but their impact might be less widespread compared to Essential Entities. Important Entities include:
- Food: Food production, processing, and distribution companies.
- Manufacturing: Manufacturers of critical products, including chemicals, medical devices, and transportation equipment.
- Digital providers: Providers of online marketplaces, online search engines, and social networking platforms.
- Research: Research organizations conducting research in critical areas such as health, energy, and cybersecurity.
Determining Applicability
While the above list provides a general overview, the specific criteria for determining whether an organization falls within the scope of NIS 2 may vary across member states. It’s crucial for organizations to consult their national implementation of the directive to confirm their obligations.
In essence, NIS 2 applies to a wide array of sectors and organizations, highlighting the criticality of cybersecurity across all facets of modern society and the economy. It’s a call to action for all entities to prioritize cybersecurity and ensure robust protection of their networks and information systems.
How NIS 2 is Applicable to Databases
In the digital age, databases and data lakes have become the repositories of an organization’s most valuable assets: sensitive customer information, intellectual property, and strategic business data. This treasure trove of information has, unfortunately, also become a prime target for cybercriminals seeking to steal and exploit this data for financial gain or to disrupt operations.
The rise of cloud computing and Software-as-a-Service (SaaS) solutions has further amplified the risks. While these technologies offer scalability and accessibility, they also expose databases to potential threats over the internet. Recent incidents have highlighted vulnerabilities in cloud-hosted databases, including inadequate network access controls, weak password management, and lack of multi-factor authentication.
Such breaches can have devastating consequences, including financial losses, reputational damage, and regulatory penalties. This is where the NIS 2 directive comes into play. With its stringent incident reporting requirements, organizations have just 24 hours to report a significant cybersecurity incident.
For databases, this means having robust Data Governance practices in place. Organizations must be able to swiftly identify which tables were potentially compromised, assess the sensitivity of the data stored within them, and determine the severity of the incident. This requires a clear understanding of data classification, data lineage, and data ownership, all of which fall under the purview of Data Governance.
In essence, NIS 2 underscores the critical role of Data Governance in protecting databases and ensuring compliance in the face of cyber threats. It’s a call for organizations to proactively manage their data assets, implement robust security measures, and be prepared to respond effectively to incidents when they occur.
Data Governance and Data Management Practices
Organizations must have robust data governance and data management practices in place to ensure the ability to identify the range and sensitivity of an attack and meet the NIS 2 directive’s strict 24-hour reporting window. These practices are essential to enabling a swift and effective response to cybersecurity incidents.
Key Practices:
- Established Data Governance Procedures: Clear and well-defined Data Governance procedures are fundamental to ensuring an organization’s preparedness for incident response. These procedures should outline roles and responsibilities, communication channels, escalation paths, and decision-making processes.
- Data Catalog and Classification: A comprehensive data catalog that indexes all critical and essential data assets, such as tables and files, is vital. This catalog should include categorization based on the sensitivity level of the information stored, enabling quick identification of impacted assets during an incident.
- Data Ownership and Stewardship: Assigning data owners and data stewards to each critical data asset ensures accountability and responsibility for data protection. These individuals should be well-versed in incident reporting procedures and play an active role in ensuring compliance.
- Data Lineage Mapping: Defining data lineage for critical data assets allows organizations to trace the flow of data from its origin to its various destinations. This capability is crucial in determining the scale of an attack, especially if data has been deleted or corrupted at the source.
- Data Observability: Implementing data observability platforms that monitor essential data assets for anomalies can provide early warning signs of potential attacks. These platforms use advanced techniques, such as anomaly detection, to identify unusual patterns or behaviors that may indicate data breaches or corruption.
By proactively implementing these Data Governance and Data Management practices, organizations can significantly enhance their ability to detect, assess, and respond to cybersecurity incidents. This preparedness is essential for complying with the NIS 2 directive’s reporting requirements and minimizing the impact of potential attacks.
Fortifying Your Data Governance: Next Steps for NIS 2 Compliance
Organizations aiming to align their data governance practices with the NIS 2 directive’s stringent requirements need to equip themselves with the right technological tools. Data management platforms play a pivotal role in ensuring compliance and bolstering cybersecurity resilience. Consider these essential capabilities:
- Robust Data Cataloging: A comprehensive data catalog is crucial for documenting and classifying all essential data assets, especially those residing in the public cloud. This catalog serves as a centralized repository of information, facilitating data discovery, understanding data sensitivity, and enabling efficient risk management.
- Data Lineage Mapping: Data lineage platforms are indispensable for tracing the intricate flow of data across various systems and processes. This capability is vital for identifying potential downstream impacts in the event of a data breach or corruption, aiding in swift incident response and containment.
- Proactive Data Observability: Data observability platforms offer real-time monitoring of essential data assets, leveraging anomaly detection to identify suspicious activity that may evade traditional network security measures. This proactive approach empowers organizations to detect and respond to potential threats before they escalate into full-blown incidents.
By investing in these data management platforms, organizations can establish a strong foundation for NIS 2 regulatory compliance. These tools enable efficient data governance, facilitate incident response, and ultimately contribute to a more secure and resilient data environment.
Remember, the NIS 2 directive is not just about meeting regulatory requirements; it’s about safeguarding your organization’s critical data assets and ensuring business continuity in the face of evolving cyber threats.

Data quality best practices - a step-by-step guide to improve data quality
- Learn the best practices in starting and scaling data quality
- Learn how to find and manage data quality issues
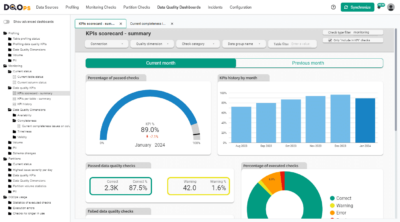
What is the DQOps Data Quality Operations Center
DQOps is a data observability platform designed to monitor data and assess the data quality trust score with data quality KPIs. DQOps provides extensive support for configuring data quality checks, applying configuration by data quality policies, detecting anomalies, and managing the data quality incident workflow.
DQOps has a configurable incident notification routing to notify the right personnel about identified data anomalies, which may be a result of a data breach. DQOps also has built-in data quality checks that scan all tables and detect sensitive information (Personal Identifiable Information) that should be protected.
You can set up DQOps locally or in your on-premises environment to learn how DQOps can monitor data sources and ensure data quality within a data platform. Follow the DQOps documentation, go through the DQOps getting started guide to learn how to set up DQOps locally, and try it.
You may also be interested in our free eBook, “A step-by-step guide to improve data quality.” The eBook documents our proven process for managing data quality issues and ensuring a high level of data quality over time. This is a great resource to learn about data quality.